Regardless of the security worries that have tormented Facebook for a considerable length of time, the vast majority are staying around and new individuals continue joining. This has driven Facebook to break records numbers with more than one billion month to month dynamic clients as of October 2012—and around 600 million dynamic day by day clients.
We share our lives on Facebook. We share our birthdays and our commemorations. We share our get-away plans and areas. We share the births of our children and the passings of our fathers. We share our most treasured minutes and our most agonizing contemplations. We disclose each part of our lives. We even racket to see the most recent forms even before they're prepared for primetime.
However, we once in a while overlook who's viewing.
We utilize Facebook as an apparatus to join, yet there are those individuals who utilize that availability for malevolent purposes. We uncover what others can use against us. They know when we're not home and for to what extent we're no more. They know the solutions for our security questions. Individuals can essentially take our personalities—and that is just with the unmistakable data we deliberately give away through our open Facebook profile.
The scariest part is that as we get more OK with advances in innovation, we really turn out to be more powerless to hacking. As though we haven't effectively done what's necessary to help programmers in their mission for our information by sharing freely, those aware of present circumstances can get into our messages and Facebook records to take each other piece of our lives that we expected to avoid prying eyes.
Actually, you don't even need to be an expert programmer to get into somebody's Facebook account.
It can be as simple as running Firesheep on your PC for a couple of minutes. Indeed, Facebook really permits individuals to get into another person's Facebook account without knowing their secret word. You should simply pick three companions to send a code to. You write in the three codes, and voilà—you're into the record. It's as simple as that.
In this article I'll demonstrat to you these, and a couple different ways that programmers (and even customary people) can hack into somebody's Facebook account. Be that as it may, don't stress, I'll likewise demonstrate to you generally accepted methods to keep it from transpiring.
The least demanding approach to "hack" into somebody's Facebook is through resetting the secret key. This could be less demanding done by individuals who are companions with the individual they're attempting to hack.
The main step would be to get your companion's Facebook email login. On the off chance that you don't definitely know it, have a go at looking on their Facebook page in the Contact Info segment.
Next, snap on Forgotten your secret key? also, sort in the casualty's email. Their record ought to come up. Click This is my record.
It will inquire as to whether you might want to reset the secret key through the casualty's messages. This doesn't assist, so with squeezing No more have admittance to these?
It will now ask How would we be able to contact you? Sort in an email that you have that likewise isn't connected to some other Facebook account.
It will now make an inquiry. In case you're dear companions with the casualty, that is extraordinary. In the event that you don't know a lot about them, make an informed supposition. In the event that you make sense of it, you can change the secret word. Presently you need to hold up 24 hours to login to their record.
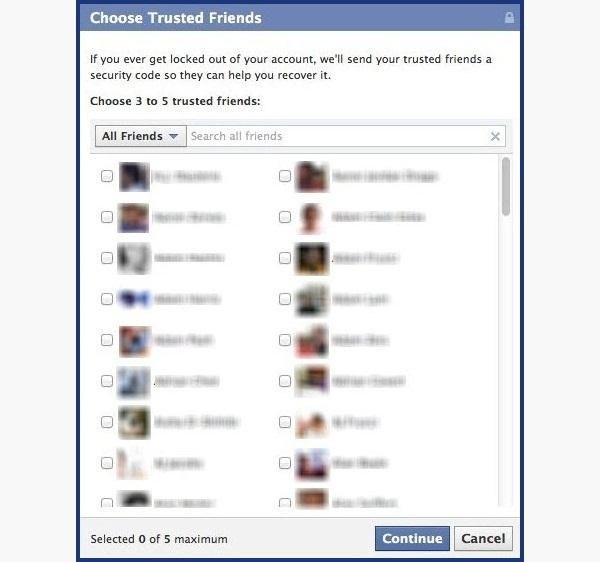
In the event that you don't make sense of the inquiry, you can tap on Recover your record with assistance from companions. This permits you to pick somewhere around three and five companions.
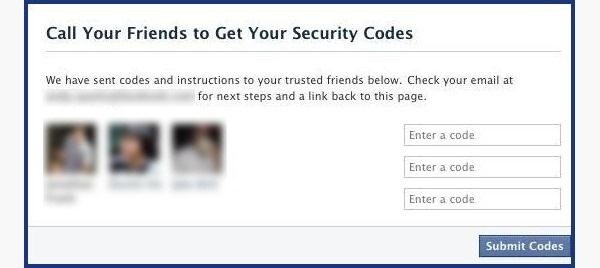
It will send them passwords, which you may approach them for, and afterward sort into the following page. You can either make three to five fake Facebook accounts and include your companion (particularly on the off chance that they simply include anybody), or you can pick three to five dear companions of yours that would be ready to give you the secret key.
The most effective method to Protect Yourself
Utilize an email address particularly for your Facebook and don't put that email address on your profile.
At the point when picking a security question and reply, make it troublesome. Make it so that nobody can make sense of it by essentially experiencing your Facebook. No pet names, no commemorations—not by any means third grade educator's names. It's as simple as looking through a yearbook.
Find out about recuperating your record from companions. You can choose the three companions you need the secret word sent to. That way you can shield yourself from a companion and other shared companions razzing you to get into your record.
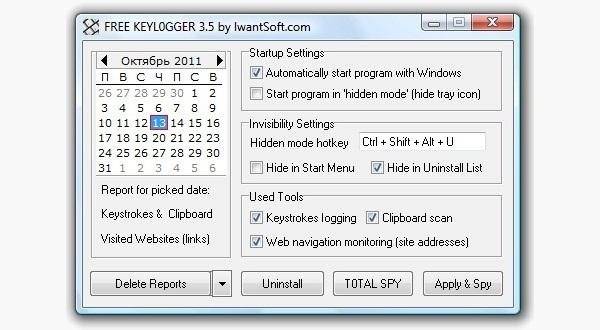
A product keylogger is a program that can record every stroke on the console that the client makes, frequently without their insight. The product must be downloaded physically on the casualty's PC. It will naturally begin catching keystrokes when the PC is turned on and stay undetected out of sight. The product can be modified to send you a synopsis of the considerable number of keystrokes by means of email.
CNET has Free Keylogger, which as the title proposes, is free. On the off chance that this isn't what you're searching for, you can hunt down other free keyloggers or pay for one.
These work the same route as the product keylogger, aside from that a USB drive with the product should be associated with the casualty's PC. The USB drive will spare a keystrokes' synopsis, so it's as straightforward as stopping it to your own PC and separating the information. You can look through Keelog at costs, yet it's bit higher than purchasing the product since you have the purchase the USB drive with the project as of now on it.
Utilize a firewall. Keyloggers more often than not send data through the web, so a firewall will screen your PC's online movement and sniff out anything suspicious.
Introduce a secret key chief. Keyloggers can't take what you don't sort. Secret key troughs naturally round out imperative structures without you needing to sort anything in.
Upgrade your product. When an organization knows of any adventures in their product, they take a shot at a redesign. Stay behind and you could be defenseless.
Change passwords. On the off chance that regardless you don't feel ensured, you can change your secret word bi-week after week. It may appear to be intense, yet it renders any data a programmer stole pointless.
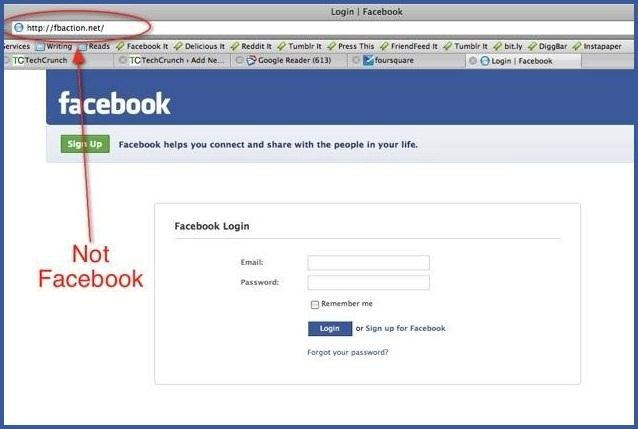
This alternative is a great deal more troublesome than the rest, however it is additionally the most widely recognized strategy to hack somebody's record. The most famous sort of phishing includes making a fake login page. The page can be sent through email to your casualty and will look precisely like the Facebook login page. In the event that the casualty sign in, the data will be sent to you rather than to Facebook. This procedure is troublesome in light of the fact that you should make a web facilitating record and a fake login page.
The most straightforward approach to do this would be to take after our aide on the best way to clone a site to make a precise of the facebook login page. At that point you'll simply need to change the submit structure to duplicate/store/email the login subtle elements a casualty enters. On the off chance that you need assistance with the accurate strides, there are definite directions accessible by Alex Long here on Null Byte. Clients are exceptionally watchful now with signing into Facebook through different connections, however, and email phishing channels are showing signs of improvement consistently, so that just adds to this officially troublesome procedure. Be that as it may, it's still conceivable, particularly in the event that you clone the whole Facebook site.
Try not to tap on connections through email. On the off chance that an email instructs you to login to Facebook through a connection, be careful. In the first place check the URL (Here's an awesome aide on what to pay special mind to). In case you're still dicey, go specifically to the principle site and login the way you more often than not do.
Phishing isn't just done through email. It can be any connection on any site/talk room/instant message/and so on. Indeed, even advertisements that appear can be pernicious. Try not to tap on any crude searching connections that request your data.
Use against infection and web security programming, as Norton or McAfee.
Treats permit a site to store data on a client's hard drive and later recover it. These treats contain critical data used to track a session that a programmer can sniff out and take on the off chance that they are on the same Wi-Fi system as the casualty. They don't really get the login passwords, yet they can even now get to the casualty's record by cloning the treats, deceiving Facebook into speculation the programmer's program is as of now confirmed.
Picture by means of wikimedia.org
Firesheep is a Firefox add-on that sniffs web activity on an open Wi-Fi association. It gathers the treats and stores them in a tab in favor of the program.
From that point, the programmer can tap on the spared treats and get to the casualty's record, the length of the casualty is still signed in. Once the casualty logs out, it is unthinkable for the programmer to get to the record.
For those with more specialized ability, look at the Same Origin Policy Facebook hack and the to some degree simpler, Facebook Password Extractor. We will proceed include more Facebook hacks sooner rather than later, so continue returning here.
On Facebook, go to your Account Settings and check under Security. Verify Secure Browsing is empowered. Firesheep can't sniff out treats over encoded associations like HTTPS, so attempt to control far from HTTP.
Full time SSL. Use Firefox additional items, for example, HTTPS-Everywhere or Force-TLS.
Log off a site when you're set. Firesheep can't stay signed into your record on the off chance that you log off.
Utilize just reliable Wi-Fi systems. A programmer can be sitting opposite you at Starbucks and looking through your email without you knowing it.
Utilize a VPN. These shield against any sidejacking from the same WiFi system, regardless of what site you're on as all your system activity will be encoded the distance to your VPN supplier.
Long range informal communication sites are extraordinary approaches to stay joined with old companions and meet new individuals. Making an occasion, sending a birthday welcome and telling your folks you adore them are each of the several ticks away.
Facebook isn't something you have to guide far from, yet you should be mindful of
We share our lives on Facebook. We share our birthdays and our commemorations. We share our get-away plans and areas. We share the births of our children and the passings of our fathers. We share our most treasured minutes and our most agonizing contemplations. We disclose each part of our lives. We even racket to see the most recent forms even before they're prepared for primetime.
However, we once in a while overlook who's viewing.
We utilize Facebook as an apparatus to join, yet there are those individuals who utilize that availability for malevolent purposes. We uncover what others can use against us. They know when we're not home and for to what extent we're no more. They know the solutions for our security questions. Individuals can essentially take our personalities—and that is just with the unmistakable data we deliberately give away through our open Facebook profile.
The scariest part is that as we get more OK with advances in innovation, we really turn out to be more powerless to hacking. As though we haven't effectively done what's necessary to help programmers in their mission for our information by sharing freely, those aware of present circumstances can get into our messages and Facebook records to take each other piece of our lives that we expected to avoid prying eyes.
Actually, you don't even need to be an expert programmer to get into somebody's Facebook account.
It can be as simple as running Firesheep on your PC for a couple of minutes. Indeed, Facebook really permits individuals to get into another person's Facebook account without knowing their secret word. You should simply pick three companions to send a code to. You write in the three codes, and voilà—you're into the record. It's as simple as that.
In this article I'll demonstrat to you these, and a couple different ways that programmers (and even customary people) can hack into somebody's Facebook account. Be that as it may, don't stress, I'll likewise demonstrate to you generally accepted methods to keep it from transpiring.
Technique 1: Reset the Password
The least demanding approach to "hack" into somebody's Facebook is through resetting the secret key. This could be less demanding done by individuals who are companions with the individual they're attempting to hack.
The main step would be to get your companion's Facebook email login. On the off chance that you don't definitely know it, have a go at looking on their Facebook page in the Contact Info segment.
Next, snap on Forgotten your secret key? also, sort in the casualty's email. Their record ought to come up. Click This is my record.
It will inquire as to whether you might want to reset the secret key through the casualty's messages. This doesn't assist, so with squeezing No more have admittance to these?
It will now ask How would we be able to contact you? Sort in an email that you have that likewise isn't connected to some other Facebook account.
It will now make an inquiry. In case you're dear companions with the casualty, that is extraordinary. In the event that you don't know a lot about them, make an informed supposition. In the event that you make sense of it, you can change the secret word. Presently you need to hold up 24 hours to login to their record.
In the event that you don't make sense of the inquiry, you can tap on Recover your record with assistance from companions. This permits you to pick somewhere around three and five companions.
It will send them passwords, which you may approach them for, and afterward sort into the following page. You can either make three to five fake Facebook accounts and include your companion (particularly on the off chance that they simply include anybody), or you can pick three to five dear companions of yours that would be ready to give you the secret key.
The most effective method to Protect Yourself
Utilize an email address particularly for your Facebook and don't put that email address on your profile.
At the point when picking a security question and reply, make it troublesome. Make it so that nobody can make sense of it by essentially experiencing your Facebook. No pet names, no commemorations—not by any means third grade educator's names. It's as simple as looking through a yearbook.
Find out about recuperating your record from companions. You can choose the three companions you need the secret word sent to. That way you can shield yourself from a companion and other shared companions razzing you to get into your record.
System 2: Use a Keylogger
Software Keylogger
A product keylogger is a program that can record every stroke on the console that the client makes, frequently without their insight. The product must be downloaded physically on the casualty's PC. It will naturally begin catching keystrokes when the PC is turned on and stay undetected out of sight. The product can be modified to send you a synopsis of the considerable number of keystrokes by means of email.
CNET has Free Keylogger, which as the title proposes, is free. On the off chance that this isn't what you're searching for, you can hunt down other free keyloggers or pay for one.
Hardware Keylogger
These work the same route as the product keylogger, aside from that a USB drive with the product should be associated with the casualty's PC. The USB drive will spare a keystrokes' synopsis, so it's as straightforward as stopping it to your own PC and separating the information. You can look through Keelog at costs, yet it's bit higher than purchasing the product since you have the purchase the USB drive with the project as of now on it.
Step by step instructions to Protect Yourself
Utilize a firewall. Keyloggers more often than not send data through the web, so a firewall will screen your PC's online movement and sniff out anything suspicious.
Introduce a secret key chief. Keyloggers can't take what you don't sort. Secret key troughs naturally round out imperative structures without you needing to sort anything in.
Upgrade your product. When an organization knows of any adventures in their product, they take a shot at a redesign. Stay behind and you could be defenseless.
Change passwords. On the off chance that regardless you don't feel ensured, you can change your secret word bi-week after week. It may appear to be intense, yet it renders any data a programmer stole pointless.
Strategy 3: Phishing
This alternative is a great deal more troublesome than the rest, however it is additionally the most widely recognized strategy to hack somebody's record. The most famous sort of phishing includes making a fake login page. The page can be sent through email to your casualty and will look precisely like the Facebook login page. In the event that the casualty sign in, the data will be sent to you rather than to Facebook. This procedure is troublesome in light of the fact that you should make a web facilitating record and a fake login page.
The most straightforward approach to do this would be to take after our aide on the best way to clone a site to make a precise of the facebook login page. At that point you'll simply need to change the submit structure to duplicate/store/email the login subtle elements a casualty enters. On the off chance that you need assistance with the accurate strides, there are definite directions accessible by Alex Long here on Null Byte. Clients are exceptionally watchful now with signing into Facebook through different connections, however, and email phishing channels are showing signs of improvement consistently, so that just adds to this officially troublesome procedure. Be that as it may, it's still conceivable, particularly in the event that you clone the whole Facebook site.
Step by step instructions to Protect Yourself
Try not to tap on connections through email. On the off chance that an email instructs you to login to Facebook through a connection, be careful. In the first place check the URL (Here's an awesome aide on what to pay special mind to). In case you're still dicey, go specifically to the principle site and login the way you more often than not do.
Phishing isn't just done through email. It can be any connection on any site/talk room/instant message/and so on. Indeed, even advertisements that appear can be pernicious. Try not to tap on any crude searching connections that request your data.
Use against infection and web security programming, as Norton or McAfee.
Strategy 4: Stealing Cookies
Treats permit a site to store data on a client's hard drive and later recover it. These treats contain critical data used to track a session that a programmer can sniff out and take on the off chance that they are on the same Wi-Fi system as the casualty. They don't really get the login passwords, yet they can even now get to the casualty's record by cloning the treats, deceiving Facebook into speculation the programmer's program is as of now confirmed.
Picture by means of wikimedia.org
Firesheep is a Firefox add-on that sniffs web activity on an open Wi-Fi association. It gathers the treats and stores them in a tab in favor of the program.
From that point, the programmer can tap on the spared treats and get to the casualty's record, the length of the casualty is still signed in. Once the casualty logs out, it is unthinkable for the programmer to get to the record.
A Couple More Facebook Hacks
For those with more specialized ability, look at the Same Origin Policy Facebook hack and the to some degree simpler, Facebook Password Extractor. We will proceed include more Facebook hacks sooner rather than later, so continue returning here.
Step by step instructions to Protect Yourself
On Facebook, go to your Account Settings and check under Security. Verify Secure Browsing is empowered. Firesheep can't sniff out treats over encoded associations like HTTPS, so attempt to control far from HTTP.
Full time SSL. Use Firefox additional items, for example, HTTPS-Everywhere or Force-TLS.
Log off a site when you're set. Firesheep can't stay signed into your record on the off chance that you log off.
Utilize just reliable Wi-Fi systems. A programmer can be sitting opposite you at Starbucks and looking through your email without you knowing it.
Utilize a VPN. These shield against any sidejacking from the same WiFi system, regardless of what site you're on as all your system activity will be encoded the distance to your VPN supplier.
Ensuring Yourself: Less Is More
Long range informal communication sites are extraordinary approaches to stay joined with old companions and meet new individuals. Making an occasion, sending a birthday welcome and telling your folks you adore them are each of the several ticks away.
Facebook isn't something you have to guide far from, yet you should be mindful of








0 comments:
Post a Comment